247 CTF Walkthrough
Crypto
My Magic Bytes
“Can you recover the secret XOR key we used to encrypt the flag?”
Knowing the properties of XOR and the magic bytes for a jpg, we can recover the key by XORing the beginning bytes of the file with FF D8 FF E0 00 10 4A 46 49 46 00 01
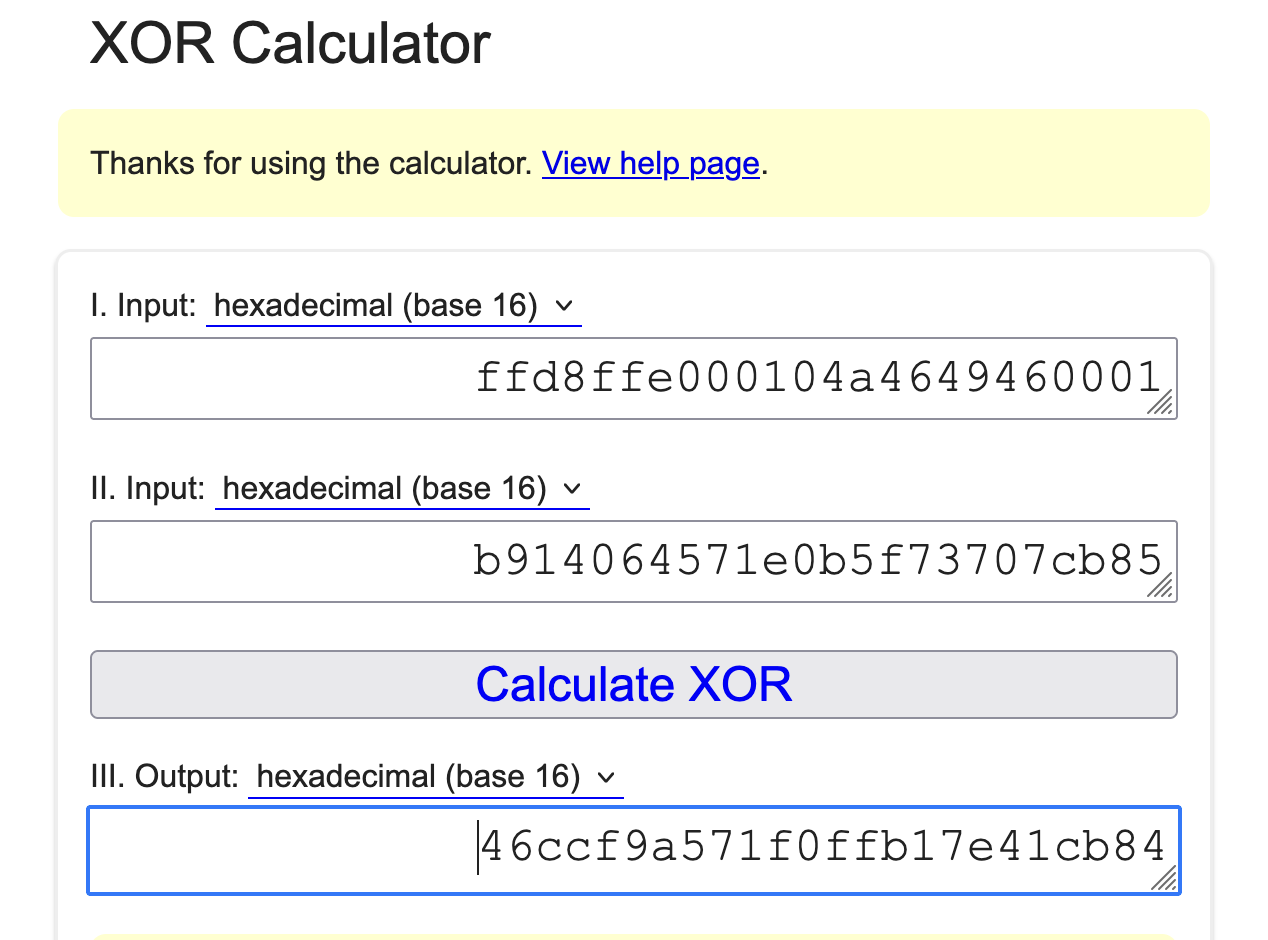
Then with the following script, we XOR the key with the file. The result of this is an image which has the flag!
with open("image.jpg.enc", "rb") as f:
data = f.read()
key = bytes.fromhex("46ccf9a571f0ffb17e41cb84")
data = bytes.fromhex(data.hex())
result = bytearray()
key_len = len(key)
for i in range(len(data)):
result.append(data[i] ^ key[i % key_len])
binary_result = bytes.fromhex(result.hex())
with open("output", "wb") as f:
f.write(binary_result)🚩247CTF{ca4e3b7f913ca7ca8f33fb050412947f}
Misc
The Text Editor Jail
“We didn’t have time to setup and test a proper jail, so this text editor will have to do for now. Can you break free?”
Use :set shell=/bin/sh|:shell from GTFO Bins
An Impossible Number
“Can you think of a number which at the same time is one more than itself?”
Integer overlow! A signed integer in c has a range of -2³¹ to 2³¹−1, so give the program 2147483647
The Flag Lottery
“Can you guess the secret number to win the lottery? The prize is a flag!”
We want to use the same code in the program to generate the secret number. Since the program uses time.time() as the seed, if we generate our own number veryyy close to the same time as the program, we’ll get the same number.